First of all, we need to understand why IP fragmentation occurs. Well, Let’s take a look at the below picture. Here, the network connecting between Router A and Router B has MTU size of 1500 bytes. The network connecting Router B and Router C has MTU size of 800 bytes.
Note:- MTU stands for Maximum Transfer Unit. As the name suggests, it is the maximum size of the packet that can be passed through the network. If the MTU size is 1500 bytes(default for Ethernet), then the particular network can carry only a packet size up to 1500 bytes (including IP header and data or payload).
Router A wants to send a packet (1500 bytes) to Router C through Router B. As the MTU of first network is 1500 bytes, the original packet can reach Router B without any problem. When Router B tries to send the original packet to Router C, it has a problem as the MTU size is 800 bytes.So, Router B needs to break the original packet into smaller packets(called fragments) in order to send to Router C. This process is called Fragmentation.

For a clear understanding of this article, I would suggest you to go through the IPv4 Header format. Below are some IP header fields which are important for fragmentation process.
Identification(16 bits): This is a unique value assigned to a packet, which helps in reassembling the fragments of the packet at the destination device. All the fragments of a single packet must have same Identification value.
Flags(3 bits): The first bit is reserved or not in use(must be ‘0’), the second bit is called DF( Don’t Fragment) and the last bit is called MF(More Fragments).
DF( Don’t Fragment) : If DF bit is set to 1 and the processing device needs to fragment the packet, then the packet is discarded. Then, the processing device sends an ICMP error message to the source. This is used for Path MTU discovery and also when the destination does not have enough resources to handle the reassembly of the fragments.
MF(More Fragments): If the value of this bit is 0, then it may be an unfragmented packet or the last fragment of an fragmented IP packet. If the value of this field is 1, then it means the packet has been fragmented and there are more fragments after this one.
Fragment offset(13 bits): This field represents the relative position of this fragment with respect to the beginning of original unfragmented IP packet in units of 8 bytes.
Note: The first fragment will have MF bit as 1 and fragment offset as 0. The last fragment will have MF bit as 0 and fragment offset as a non-zero value. All other fragments(in between first and last fragments) will have MF bit as 1 and fragment offset as a non-zero value.
Original Packet:
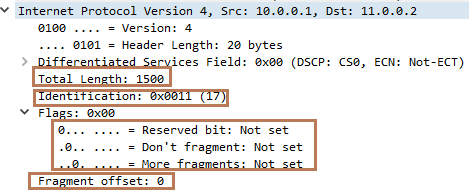
Now, let’s focus on our original example. Below is the Wireshark capture of the original packet (while moving from Router A to Router B). You can see:
Total length of the packet is 1500 bytes( 20 byes header and 1480 bytes of payload).
Identification field has a value of 17. You will see all the fragments will carry the same Identification value till it reaches destination. This value is set by the source of the packet (i.e. Router A).
Flags has value of 0 as MF bit is 0(as the packet has not been fragmented).
Fragment Offset has a value of 0 as the packet has not been fragmented.
First Fragment:
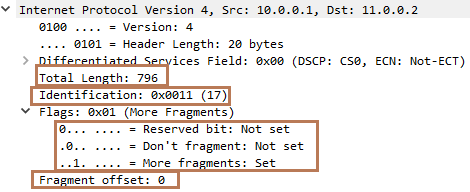
As the second network has an MTU of 800 bytes, Router B fragmented the original packet into two fragments. Below is the wireshark capture of first fragment. You can see:
Total length of the packet is 796 bytes( 20 bytes of header and 776 bytes of payload). You might be wondering why the total length is not 800 bytes. Well, the payload size of the packet must be less than 780 bytes (as header size is 20 bytes) and must be multiple of 8 as fragment offset carries a value in units of 8 bytes. So, 97*8=776(which is less than 780).
Identification field has a value of 17.
Flags has value of 1. MF bit is set to 1 as there is another fragment following this one.
Fragment Offset has a value of 0(The position of the first byte of the fragment in relation to the original packet is 0 as this is the first fragment)
Second Fragment:
Below is the wireshark capture of second or last fragment. You can see:
Total length is 724 bytes as (20 bytes of header and 704 bytes of payload). The first fragment has already carried 776 bytes, so we have only 704 bytes left out of 1480 bytes.
Identification field has a value of 17.
Flags has value of 0. As this is the last fragment, the MF bit is 0.
Fragment Offset will have a value of 97 as the position of the first byte of this fragment in relation to the original packet is 776th byte(97*8=776). However, Wireshark displays the fragment offset value by multiplying 8, so the value is 776 here.

Important points:
- Any router can fragment a packet on the way to the destination. However, only the destination device will do the reassembly of the packet.
- If at least one fragment is dropped or corrupted before it reaches to the destination, then the original packet needs to be re-transmitted, which causes excessive retransmission during congestion.
- IP fragmentation can be avoided by using Path MTU discovery.

Very nice