Encryption: Encryption is a method in which plain text or a message is converted to an encoded version , so that only the intended person can decode it. The encoded message is called cipher text.
Decryption: Decryption is exactly opposite of encryption. It is the method of converting a encoded message(cipher text) to plain text.
Cipher: Cipher is the algorithm used to encrypt or decrypt a message. Cipher takes the help of a key (a number) for it’s operation.
There are two types of encryption schemes used in modern cryptography.
- Symmetric key Encryption
- Asymmetric key Encryption
1. Symmetric key Encryption: Symmetric encryption uses a single key(also called shared secret) for both encryption and decryption. Below is an example of symmetric key encryption.
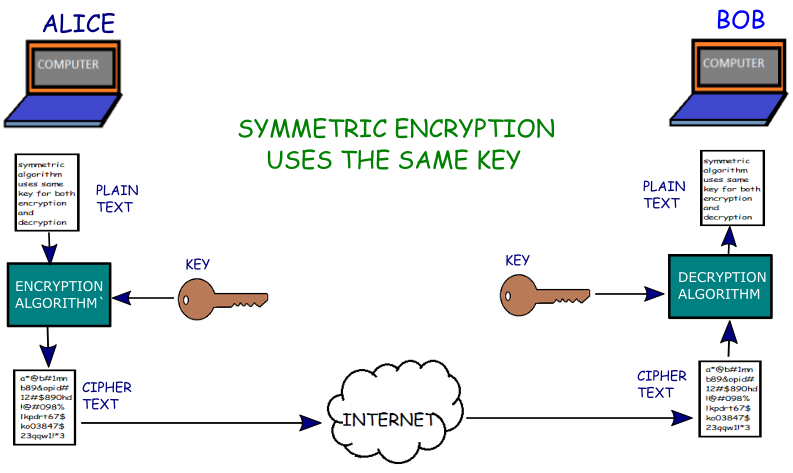
Here, Alice wants to send a confidential message to Bob through Internet. However, anyone can read the message(as it is in plain text) with the help of a packet analyser as the message travels through the internet. So, Alice and Bob decided to use symmetric key encryption to maintain privacy. Either Alice or Bob should generate a secret key and share it to other. Once Alice has the key, she used a symmetric algorithm and the shared secret key(only known to Alice and Bob) to encrypt the message as shown in the picture above. The encrypted message is called cipher text. Now, Alice sends the cipher text to Bob through the untrusted medium like Internet. Even though an attacker can see the encrypted message, but he can not read the message as it is completely scrambled. He needs the secret key to decrypt the message (which he doesn’t have) to read it.
As the encrypted message reaches to Bob, he uses the same algorithm and same key to decrypt the cipher text to plain text. Now, Bob can read the message. The secret key must be kept private and should be only known to Alice and Bob.
Advantage: This method is very simple and takes very less time to encrypt and decrypt the message. This method is usually preferred when transferring huge amount of data(bulk data transmission).
Disadvantage: The major disadvantage of this method is in exchanging the secret key to the the other party. If anyone else finds this key during exchange, then confidentiality of the message will be lost.
Another drawback of this method is the increase in the number of keys as the users increase. When there are only 2 users(for example, A and B), we need only one key for a secure connection. When there are 3 users(A, B and C), we need a key for A and B, another key between B and C; and another key between A and C. So totally 3 keys are needed. When there are 4 users, we need 6 keys. so, when there are ‘n’ users, we need n(n-1)/2 number of keys for symmetric encryption. For 100 users, we need 4950 keys.
Symmetric Encryption Algorithms: RC4, DES, 3DES,AES etc.
2. Asymmetric key Encryption: Asymmetric encryption uses two different keys for maintaining privacy. If a message is encrypted with one key, then it can be only decrypted with other key in the key pair. The keys are called public key and private key.
Public key: This key is shared with everyone who wishes to exchange massage.
Private Key: This key is kept secret and is not shared with anyone. If this key is compromised, then the confidentiality of the message is lost.
Asymmetric encryption is also called public key cryptography. Below is an example of the asymmetric key encryption.

Here, Alice wants to send a confidential message to Bob through Internet. However, anyone can read the message(as it is in plain text) with the help of a packet analyser as the message travels through the internet. This time, Alice and Bob decided to use asymmetric key encryption. So, both Alice and Bob generated their own Public and private key pairs; and shared the public key to each other. Please note that they will not share the private key with each other.
Now, Alice used an asymmetric algorithm and Bob’s Public key to encrypt the confidential message(plain text). Then, she sent the cipher text to Bob through Internet.Even though an attacker can see the encrypted message, but he can not read the message as it is completely scrambled. He needs the Bob’s secret key to decrypt the message (which he doesn’t have) to read it.
As the encrypted message reaches to Bob, he uses the same algorithm and his private key to decrypt the cipher text to plain text. Now, Bob can read the message.
If Bob wants to send a message to Alice, then Bob should use Alice’s public key to encrypt the message. Then, Alice can use her private key to decrypt it.
Note:-In asymmetric encryption, a person can encrypt a message using the receiver’s public key; and the encrypted message can only be decrypted with the receiver’s private key.
Advantage: Asymmetric encryption provides more security as compared to symmetric encryption as the private key is never shared with anyone. So, asymmetric encryption is generally used for exchanging the shared key between the parties in an unsecured medium like internet.
It also requires less number of keys as compared to symmetric encryption as the number of users increases.When there are only 2 users(for example A and B), we need 2 keys(private and public) for A, and 2 keys(private and public) for B. So, totally 4 keys needed for 2 users. When one more user (C) is added, we need 2 more keys for C along with 2 keys for A, and 2 keys for B. So, totally 6 keys needed for 3 users. When there are ‘n’ users, we need 2*n number of keys for asymmetric encryption. For 100 users, we need 2*100=200 keys (as compared to 4950 keys in symmetric encryption) .
Disadvantage: Asymmetric algorithms are very complex, and it requires comparatively more time than symmetric algorithm.
Asymmetric Encryption Algorithms: DSA,RSA, Diffie-Hellman etc.
Use case of both the encryption Methods: SSL/TLS uses both the methods for its operation. Firstly, It uses asymmetric encryption for exchanging a shared key to the other party. Then, It uses symmetric encryption for sending the actual data/message.
Hey
Hello.
Good information..really helpfull…!